Gartner’s defines security orchestration, automation and response (i-SOAR) as technologies that enable
organizations to take inputs from a variety of sources (mostly from security information and event management [SIEM]
systems) and apply workflows aligned to processes and procedures.
Our i-SOAR product is orchestrated via integrations of Assetie, Netra, and VAMA with other 3
rd party technologies and
is automated to achieve the desired outcome and greater visibility.
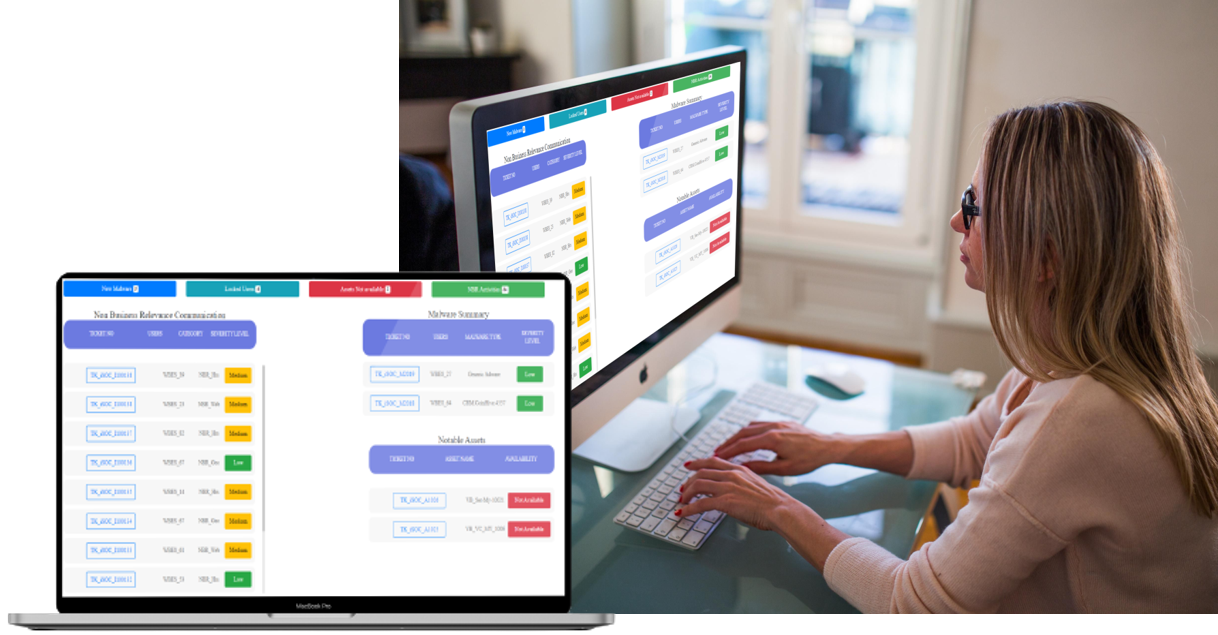
Additional capabilities include case and incident management features;
the ability to manage threat intelligence, dashboards, and reporting;
...
and analytics that can be applied across various functions. i-SOAR tools significantly enhance security operations
activities like threat detection and response by providing machine-powered assistance to human analysts to improve
the efficiency and consistency of people and processes.
Read more